In an increasingly interconnected world, the cybersecurity landscape is transforming at an unprecedented pace. Cyber threats are no longer simple malware attacks or isolated security breaches; they have evolved into sophisticated, multi-layered strategic operations that can compromise entire organisational ecosystems. One good thing is while the threat landscape is changing contrary to the narrative that exists not many variations are being observed in real world attacks.
Key Emerging Threat Vectors:
1. Artificial Intelligence-Powered Attacks
Cybercriminals are now leveraging artificial intelligence to create more intelligent and adaptive attack strategies. The various ai services enable:
- Sophisticated phishing campaigns that mimic human communication patterns
- Advanced social engineering techniques
- Automated vulnerability discovery
- Intelligent malware that can adapt to security environments
- It also makes attacks cheaper as the bad actors can function more efficiently.
Case Study: Emotet Malware (AI-Driven Phishing)
Emotet, one of the most notorious malware families, has evolved to use AI techniques for phishing. It leverages machine learning to craft convincing and targeted phishing emails by learning from past communications. These AI-powered phishing attempts are so advanced that they often bypass traditional email security systems.
Statistics:
- According to a 2024 report by the European Cybersecurity Agency, AI-powered attacks have increased by 40% year over year, with phishing attacks being the most common method.

2. Supply Chain Vulnerabilities
Modern cyber attacks are increasingly targeting complex supply chain networks. By compromising a single vendor or third-party service, attackers can potentially infiltrate multiple interconnected organisations simultaneously.
Key risks include:
- Sophisticated software injection techniques
- Compromised software update mechanisms
- Strategic infiltration of technology providers
- Long-term, undetected network access
Case Study: SolarWinds Attack
In December 2020, the SolarWinds cyberattack exposed the vulnerability of supply chains. Hackers gained access to SolarWinds’ software update mechanism, infecting thousands of organisations, including U.S. government agencies and private sector companies. This attack demonstrated how an intrusion into one supply chain can have far-reaching consequences.
Statistics:
- A 2023 report by CrowdStrike highlighted that 74% of organisations reported at least one supply chain attack in the last year, showing the growing prevalence of this attack vector.
3. Quantum Computing Threats
The emerging quantum computing landscape presents both opportunities and significant cybersecurity challenges:
- Potential to break current encryption standards
- Advanced cryptanalysis capabilities
- Rapid decryption of traditionally secure communication channels
- Unprecedented computational power for breaking complex security protocols
- Potential for steal encrypted data now which can later be decrypted later a likely vector.
Case Study: The Race to Post-Quantum Cryptography
Governments and companies globally are investing heavily in research on post-quantum cryptography to future-proof their encryption methods against quantum computing’s potential to break current encryption systems. IBM, Google, and the U.S. National Institute of Standards and Technology (NIST) are all working on standardising quantum-resistant encryption algorithms.
- The U.S. government has allocated over $1 billion in funding through its National Quantum Initiative to accelerate research into quantum computing and its impact on cybersecurity.
4. Internet of Things (IoT) Vulnerabilities
The proliferation of IoT devices has dramatically expanded the potential attack surface:
- Unsecured smart home devices
- Industrial control systems with minimal security configurations
- Medical devices with network connectivity
- Connected automotive systems
Case Study: Mirai Botnet Attack
The Mirai botnet attack in 2016 was a wake-up call regarding IoT vulnerabilities. The botnet, consisting primarily of unsecured IoT devices, launched one of the largest DDoS attacks in history, impacting major internet platforms like Dyn, causing widespread outages.
- According to a 2023 report by Kaspersky, 45% of all IoT devices are vulnerable to basic attacks, with inadequate security measures being the primary cause.
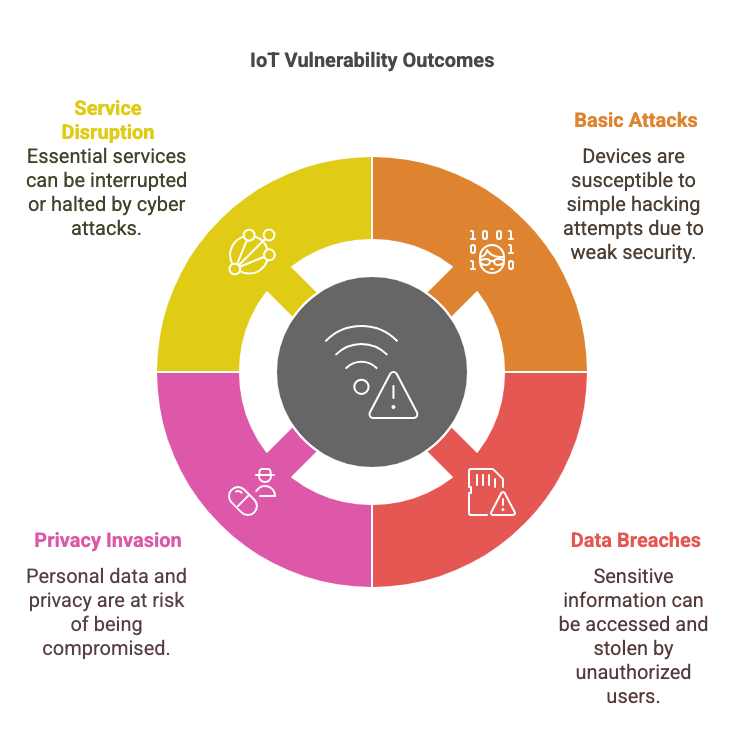
5. Geopolitical Cyber Warfare
Nation-state sponsored cyber operations are becoming increasingly sophisticated:
- Strategic infrastructure targeting
- Cyber espionage campaigns
- Sophisticated disinformation strategies
- Economic disruption through digital means
- Sanctioned countries stealing money to fund themselves.
Case Study: NotPetya Cyberattack (Ukraine, 2017)
The NotPetya attack, believed to be a state-sponsored cyberattack from Russia, targeted Ukrainian infrastructure but spread globally, impacting major corporations such as Maersk and Merck. The attack was disguised as ransomware but was actually a destructive form of cyber warfare, causing billions in damages.
- A report by the Council on Foreign Relations noted that 90% of nation-state cyberattacks are aimed at disrupting infrastructure, espionage, or economic damage.
Emerging Defense Strategies
Example:
The FBI’s “Internet Crime Complaint Center” (IC3) works with private and public sectors to track emerging threats. In 2023, the IC3 identified over 800,000 reported cybercrimes.
Zero Trust Architecture
Traditional perimeter-based security models are becoming obsolete. Zero Trust principles mandate:
Example:
In 2024, Google announced it had fully transitioned to a Zero Trust model for its cloud infrastructure, reducing the impact of insider threats by 70%.
Artificial Intelligence Defense Mechanisms

Example:
Darktrace, an AI-driven cybersecurity company, detected an attack in 2023 by recognizing abnormal behavior within a network and stopping a ransomware attack before it could escalate.
Recommendations for Organizations
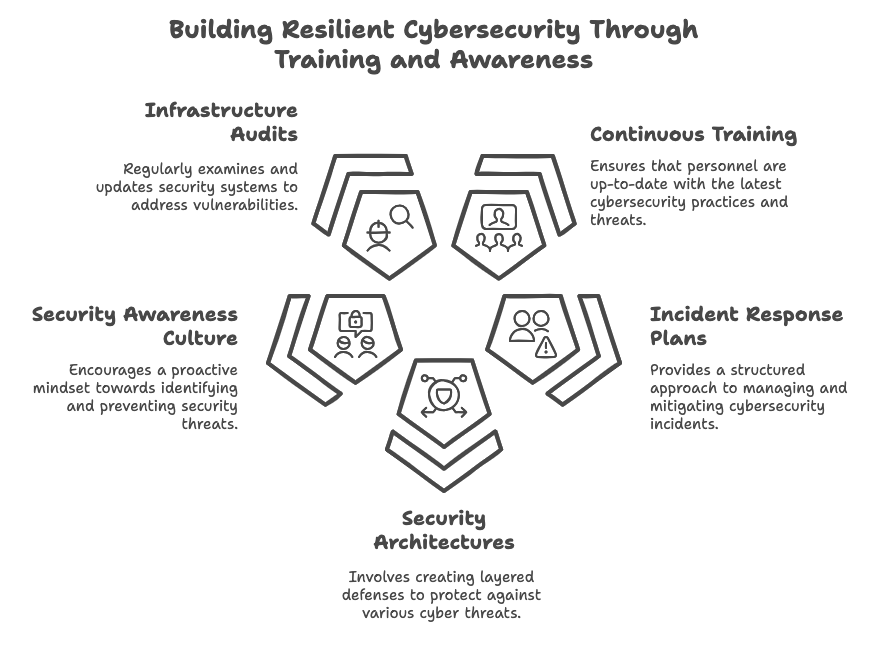
- Invest in continuous cybersecurity training.
- Develop robust incident response plans.
- Implement multi-layered security architectures.
- Foster a culture of security awareness.
- Regularly audit and update security infrastructure.
The emerging cyber threat landscape demands unprecedented levels of vigilance, adaptability, and strategic thinking. Organisations must view cybersecurity not as a static defense mechanism, but as a dynamic, continuously evolving discipline.
Success in this new digital battlefield requires a holistic approach that combines cutting-edge technology, human expertise, and strategic foresight.